Tips to Protect from Ransomware

Tips to Protect from Ransomware
The year of 2017 has been plagued with ransomware attacks. We had the massive infection of Wannacry ransomware in May and subsequently the Bad Rabbit ransomware that just came out few days ago. With the greater embrace of cryptocurrencies such as the Bitcoin and Ethereum that offer great anonymity for payment transactions, we can reasonably expect more ransomware to be spread in the wild through more and more creative ways to induce victims into falling prey as hackers have monetary motivation aided by cryptocurrencies.
How does this impact SMEs & Business Owners?
SMEs and Business Owners are likely to own lots of internal and customer data on staff computers, as well as office shared drive. This group of users are highly vulnerable due to the lack of Business Continuity Plan or Disaster Recovery Solution. The data within the staff computers or shared drive are likely to be the only copy they have, making them completely defenseless against ransomware attack — once the files are locked up, they have no choice but to pay the ransom to decrypt the files they need.
A full suite of disaster recovery & information security solution can be very costly, making the entry barrier high for most SMEs unfortunately. The goal of this article is simple: We want to share the lowest cost method (best where possible — FREE) that SMEs should adopt as their first line of defence against the ransomware.
Tips #1 User Awareness & Alertness
If you receive an email containing an attachment from someone you do not know, DO NOT open the attachment.
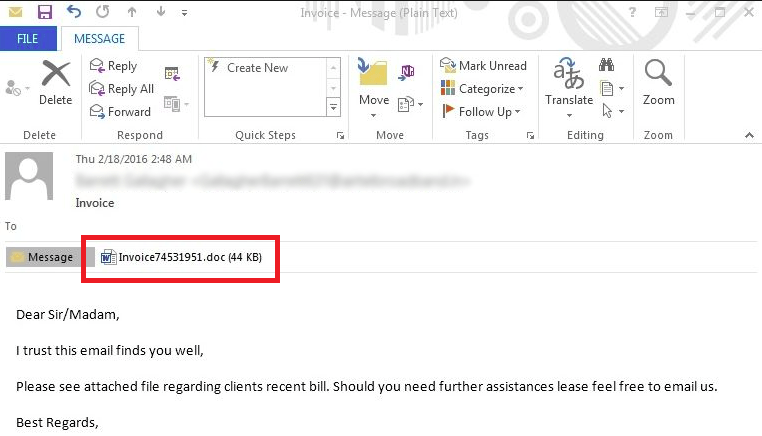
If you receive an email from someone you know (the name & email address appear correct) but you are not expecting to receive any attachment from them, try to call or send a Whatsapp message to the person to verify if the email is genuine. If you are unable to reach out to the person:
- If the person is not in any position to send you a Quotation, Purchase Order, Invoice or Delivery Order (typically used traps), DO NOT open the attachment.
- If the email contains an executable (.exe) attachment or you have not seen the file format before (such as .ecc, .ezz, .exx, .zzz, .xyz, .aaa, .abc, .ccc, .vvv, .xxx, .ttt, .micro, .encrypted, .locked, .crypto, _crypt, .crinf, .r5a, .XRNT, .XTBL, .crypt, .R16M01D05, .pzdc, .good, .LOL!, .OMG!, .RDM, .RRK, .encryptedRSA, .crjoker, .EnCiPhErEd, .LeChiffre, .keybtc@inbox_com, .0x0, .bleep, .1999, .vault, .HA3, .toxcrypt, .magic, .SUPERCRYPT, .CTBL, .CTB2, .locky), DO NOT open the attachment.
- If you open the attachment and the program such as Microsoft Excel asks for further security permission, DO NOT allow the security access level.
The tricks above have been used to exploit millions of victims through the Wannacry ransomware.
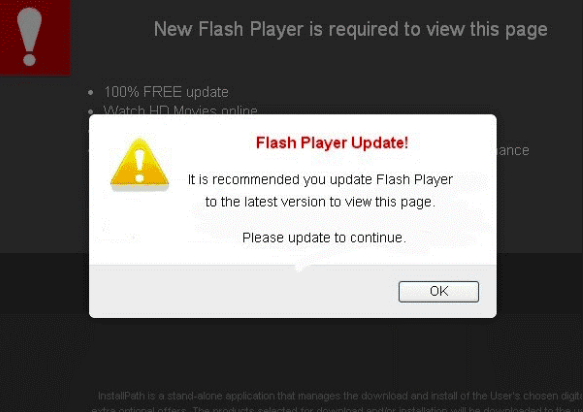
Now if you happen to be surfing some websites and you see certain pop-up asking you to upgrade your Adobe Flash or Java version, DO NOT approve anything. Close your browser immediately.
Tips #2 Protection Tools
Yes, we know that to err is human and we are bound to let things slip through no matter how careful or alert we are. This is where we need good security protection tools to help us minimise the risks. There are two essential tools which are really affordable that you should consider using.
- Eset Smart Security
You might have heard of or used their NOD32 Antivirus for home. In business environment, their products are still highly relevant and useful. While your friends may have a lot to share about their own preferred antivirus (likely to be from Kaspasky, Symantec, Intel McAfee, Trend Micro, AVG, Avira, to name a few) we are more inclined to recommend Eset to our customers as it has not failed us once be it for our own protection or for our infrastructure protection with their security solutions for server. Let’s not forget that they are among the first to detect the Bad Rabbit ransomware this time.
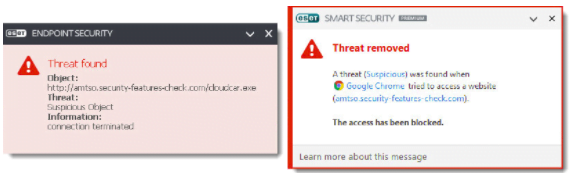
With Eset’s LiveGrid, the software gets more intelligent by learning the latest threats from other Eset users in this world, usually threats that are so new that their official virus definition list still does not contain it. This is particularly useful against new ransomware — and if your users accidentally downloaded a ransomware, it will be blocked automatically and you should see the following prompt:
As this article is written for SMEs and Business Owners, we recommend you to consider either Eset Internet Security (MSRP SGD$39/User/Year) or if you have more than 25 users, consider Eset Endpoint Protection Advanced (MSRP SGD$66/User/Year). Both these two editions give sufficient protection to most SMEs (they are more than just antivirus) and the major difference is the Endpoint Protection allows a centralised management of all the Eset-protected computers, making it a lot easier to perform entire office virus scanning or virus update at ease.
You can get the licence from your local computer shops in Singapore/Malaysia/Thailand or if need to, feel free to contact us for a quote.
- Barracuda Email Security Gateway
Barracuda is renowned for its strong RBL that is very effective in eliminating lots of spam mails received by corporate email users. However, their Email Security Gateway delivers more than just antispam technology. If you study the technical architecture of their appliance, you will discover that every email goes through 12 layers of defense before they are rated with “Good” and reach your mailbox.
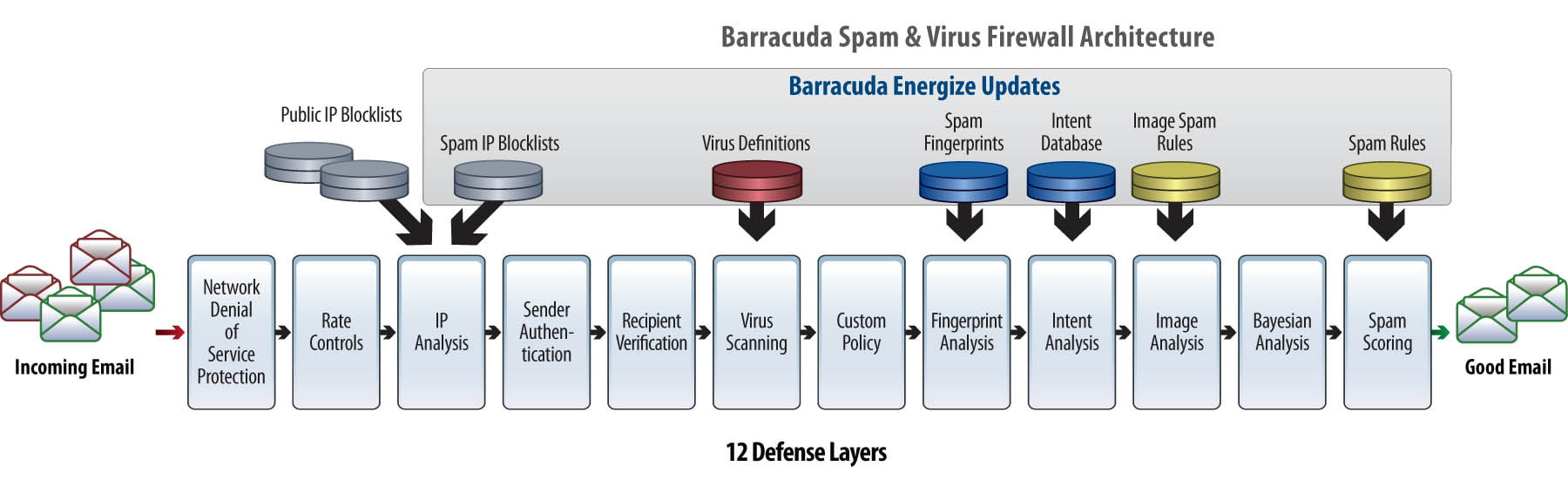
Similar to ESET, Barracuda’s appliance is also actively learning the latest threat from other appliances globally, including protecting from the latest ransomware spread via email. Once a ransomware is spotted and learned, any emails containing similar patterns will be filtered away, and do not enter your Inbox at all.
Traditionally Barracuda has been sold as a hardware appliance (in layman term, a server hardware on its own) that should be installed in front of any mail server such that the emails are first routed into the appliance before they are further routed to your mailbox. For customers in the US, they have virtual appliance licence available to be installed onto virtual or physical servers. They typically cost anywhere from several thousand US dollars to several ten thousand US dollars per year to maintain, depending on the scale required.
Yes, for SMEs the figures above can be scary. However, we can help you protect your mailbox (any mailbox, hosted with any service providers) with Barracuda for as low as SGD$1.00/user/month. Feel free to contact us for a quote.
Tips #3 Backup important files into NAS, and backup NAS further!
Now that you have learned the Preventive (Tips #1) and Protective (Tips #2) measures, it is also important to be prepared for the worst — what if the ransomware slip through human eyes, Eset Smart Security and Barracuda all at the same time, making you among the first unlucky victims of ransomware in the world? The chances are slim but they are not impossible!
If you keep extra copies of your important files into a Network Attached Storage (NAS), you can retrieve the files from NAS if the ones on your computer are infected with ransomware. At this juncture, a lot of you should be thinking: I simply cannot make it a habit to systematically copy important files to the NAS so most likely when I am infected with malware, the files on NAS are either too old or they do not have what I want!
Yes, this is a typical human habit at workplaces – and there is definitely an automated software that does this.
NAS today are getting a lot smarter and they are a lot more powerful than the “mapped drives” or “Z:” that you might be familiar with in most office environments. For NAS, we prefer the products by Synology. Besides being a “mapped drive” for you to share files with colleagues within the office or even customers/suppliers over the internet, they have a backup software for computers which helps you perform a backup on your important files, quietly as you use your computer.
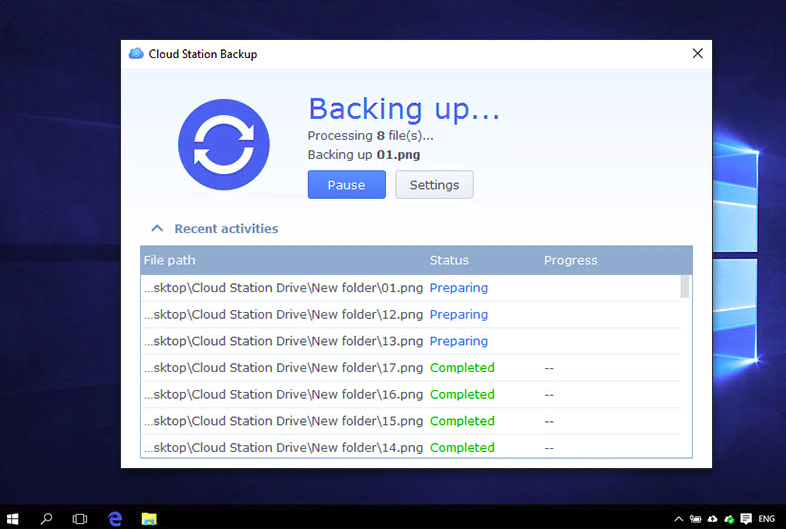
Now if everyone within the office performs a backup of their important folders and files into the NAS, this is where they can retrieve their files during an unlikely event of a ransomware attack.
Would there be a possibility that even the Synology is infected with ransomware, therefore making the files within NAS affected? Yes, it is possible. Fortunately, with Synology Snapshot Replication, which in layman terms you are able to configure Synology NAS keep a backup copy of itself at fixed time interval, for a period of time, both defined by you. For instance, if you enable Snapshot Replication to run once every Hourly and you keep the replication for 30 days, you are able to roll back every hourly changes of the files, up to 30 days from the day of attack, giving you ample of time to get back the files in the state before they are infected!
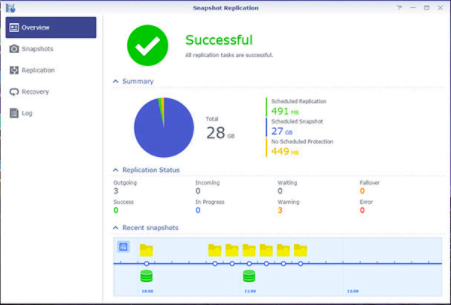
Cost wise, they are made affordable for SMEs. You may consider two configurations below:
- The best value setup with approximately 6TB usable space (RAID-1): 1x 2-bay Synology DS216j (MSRP S$271) with 2x 6TB Western Digital Red Pro (MSRP S$870) = S$1,141 one time fee, for life
- The better setup with approximately 8TB usable space (RAID-6): 1x 4-bay Synology DS418j (MSRP S$474) with 4x 4TB Western Digital Red Pro (MSRP S$1,404) = S$1,878 one time fee, for life
The best value setup above can afford 1 out of 2 HDDs to fail before your data is gone while the better setup option can afford 2 out of 4 HDDs to fail. You can get them from your local computer shops in Singapore/Malaysia/Thailand.
We hope you find this article useful and please share this article with your friends/co-workers/customers/suppliers because if they stop ransomware from attacking their computer, they definitely will not spread the ransomware to you. So help them with these 3 tips if you can!
SecureAX is a Fully Managed Cloud Server provider in Singapore & Thailand which specialises in high performance and high security platforms. Contact us to find out how we can help you with your IT security protection!